Network Security Solution
A fast, reliable and well secured network is of crucial importance to any organization. DVW is the answer to this challenge using leading edge IP flow monitoring technology (NetFlow, IPFIX) to give you the best solution for network visibility.


Security Audits
Security audit is a manual or systematic measurable technical assessment of a system or application.
Vulnerability Prevention
Companies most use software security practice to respond to an attack, least use practice to prevent the introduction of a vulnerability.
Security Analysis
Security analysis is the analysis of tradeable financial instruments called securities. It deals with finding the proper value of individual securities

About
Security Solutions & Services
Ensure the security of your systems through our solutions or services in cyber security. The security experts team in DVW examines internal networks, wireless networks (WiFi), systems and applications (web and mobile) with the goal of identifying potential vulnerabilities which could be exploited by dangerous entities.
SOFTWARE CODE AUDIT
DVW provides software code audits in automated, manual, execution and static modes, finding critical issues and weaknesses in the source code before they become actual vulnerabilities.
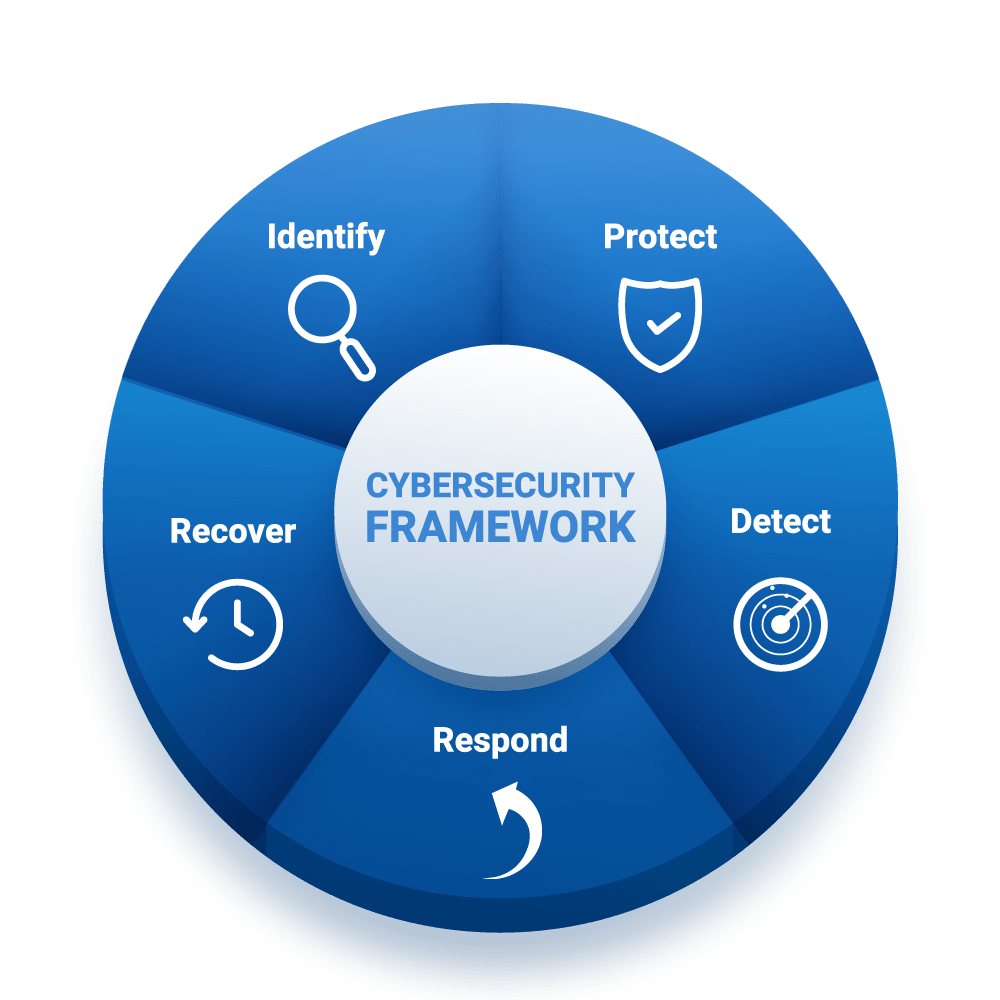
Features
What We Offer
Ensure the security of your systems through our solutions or services in cybersecurity.
SECURITY ASSESSMENTS
The security experts team examines internal networks, wireless networks (WiFi), systems and applications (web and mobile).
VULNERABILITY MANAGEMENT
provides continuous vulnerability monitoring services: Vulnerability scanning in networks,.
SVM SOLUTIONS
With the help of SVM (Software Vulnerability Management) solutions, we have the goal.
Approach
Our Approach to
SIEM SOLUTIONS
The SIEM solutions DVW, offers allow to detect both in-house (coming from employees) and external (cyber criminals) threats when software vulnerabilities are involved.
SIEM solutions act when prevention measures are not enough. They raise security alerts in real time based on events and patterns, which allows to prevent even the most complex attacks.
Threat prevention even when they are not based on vulnerabilities. (Malware, Reverse Engineering, Information Leakage, Denial of Services…).
Information is gathered from security devices such as Firewalls, IDS/ IPS, WAFs, IP Cameras, Workstations…

Contact Us
+92 49 2723782
Haji Park, Quadiwind Road, Kasur, Pakistan
Monday-Friday: 8am – 5pm
Get Started
Need assistance, contact us, and we shall stand with you until your problems are resolved.
